- Analytics and Tracking, Consumer products, Customer Experience, Data visualization, Design, Design Tools and Software, Healthcare, Input devices, Location-Based Services, Marketing and Brand, Mobile Applications, Mobile Technology, New and Emerging Technologies, Privacy and Data Security, Product design, Product Releases and Redesigns, Tablet
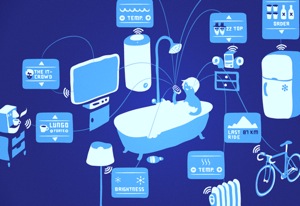
As radio frequency identification tags become more cost effective, a smart fridge might emerge that is able to take full advantage of the Internet of Things
Article by Avi Itzkovitch
Share:The Internet of Things and the Mythical Smart Fridge
Share this link
- September 18, 2013
12 min read